Identity Protection

SMARTJAC smart card management eval Kit for SME business
SMARTJAC smart card management eval Kit - Smart Card Management SW+HW solution for small and medium size business.
IDProve 400 - Protiva Thin OTP Reader
*Unconnected OATH smartcard reader *PIN/ no PIN Profiles support *The credit card- sized fits in a wallet along with Corporate Badge *Ultra Light and portable *Customizable (Logo, Colors, Keypad, , etc ...).
.NET Solution Securing Offices and Networks
With the .NET range (minidriver smart card), organizations can easily leverage advanced and proven smart card technology to secure their networks end-to-end, whilst dramatically reducing implementation costs and complexity.
SAS - Authentication Service - OTP platform
Building on award-winning SafeNet Authentication Service, SMARTJAC is now offering SafeNet Trusted Access, a new access management service that makes it easy to manage cloud access with cloud single sign-on, scenario-based access policies and multi-factor authentication—all from the same management platform.
MobiOTP
Two-Factor Authentication on mobile utilizing Taisys' unique, patented SIMoME™ technology slim SIM, allows the addition of two factor authentication into mobile phones already on the market or owned by users.
SafeNet OTP 110 One-Time Password Token
SafeNet OTP hardware tokens provide a strong and scalable foundation for securing access to enterprise, web-based and cloud applications, and complying with privacy and security regulations.
SafeNet hardware tokens offer rich case-branding options, and are field-programmable by the customer, enabling organizations to maintain stringent control over their own critical OTP security data.
A secure and convenient OTP token for protecting your network identities.
SafeNet OTP 110 is a cost effective OATH-compliant OTP hardware token that features waterproof casing, and enables
two-factor authentication in time-sync and event-based modes.
tPro ECC secure usb token
tPro ECC is a small, user-friendly device for authorizing electronic funds transfers. It is embedded with certificates and private keys based on the Elliptic Curves Cryptography (ECC) mechanism, one of the best solutions for the future-proof secure systems.
tPro OTP
tPro OTP is a small and user-friendly device that generates and automatically inputs one-time passwords, based on the HOTP (HMAC) algorithm. There is no need to rewrite passwords from a card or a screen, so they can be much longer which increases security.
tPro OTP may be used in banking, but it can have other purposes too. Apart from verifying transfers and operations, it can be useful in all the situations, where a username and a password are not enough.
Smartphone and Software Token Authenticators
Mobile authentication solutions provide the security of proven two-factor strong authentication with the convenience, simplicity, and ease of use of OTPs generated on personal mobile devices or PCs.
Offering the convenience of phone-as-a-token authentication, PUSH OTP software authentication for tablets and mobile phones.
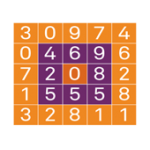
Grid Authenticator - Pattern-based Authentication
Tokenless technology enables any user to be authenticated anytime and anywhere. Context-based authentication offers convenient, frictionless strong authentication while maintaining the flexibility and agility to add protection with stronger methods of security in higher risk situations. Combined with “step-up” authentication, context-based authentication optimizes a layered approach to access security by assessing user login attributes and matching them against pre-defined security policies.
Context-based Authentication
Context-based authentication enables effective risk management by requiring an additional authenticator factor only in high risk situations, lowering the barrier for strong authentication and enhancing user convenience.
Context-based or contextual authentication is central to creating compliance based access policies and preventing security fatigue. Taking into account variables, such as your network, location and operating system, contextual data provides additional information on a login attempt, and fires the appropriate access policy.
By assessing a user’s contextual login attributes, single sign on and access management solutions can continuously match the level of authentication required from the user with the access policy defined for each application.
Hardware-Based OTP Authenticators
OTP hardware tokens used to generate highly secure one-time passwords, ensuring that only properly authenticated users are authorized access to critical applications and data.
Out-of-Band Authenticators
Delivered by SMS text messages or email, out-of-band authentication reduces the administrative overhead of a strong authentication solution by removing the need to distribute hardware or install software.